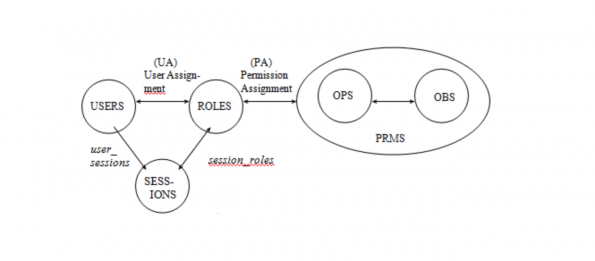
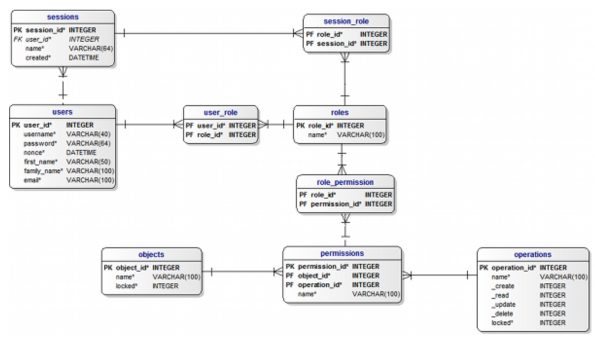
RBAC
Role Based Access Control (RBAC) is a model for giving a user access to one or more resources.
NIST CSRC RBAC is the de facto implementation [1].
Introduction
RBAC is an access control mechanism which:
- Describes complex access control policies,
- Reduces errors in administration,
- Reduces cost of administration.
- Model and Entity Relation taken from Mind-it [2].
- Model Database: https://www.mind-it.info/wp-content/uploads/2011/06/mysql_5.txt
- Model PHP: https://www.mind-it.info/2009/10/02/a-query-engine-for-php
Examples
As always an example makes more clear than anything else.
Generic example
Suppose we take a generic app as an example. The following fictive user and roles are defined:
|
|
Specific example
The above generic example has a few disadvantages.
- The application may have different roles for different occurrences in an application.
- The object may have different roles for specific objects inside an application.
In case of the application Energy the user may have different houses and have different roles on those houses. I call that a filter.
| User | Role | Filter |
|---|---|---|
| Harm | Admin | NOH-116 |
| Admin | AadR-2 | |
| Admin | OST-16 | |
| Riet | Writer | NOH-116 |
| Reader | AadR-2 | |
| OST-16 | ||
| Jan | NOH-116 | |
| AadR-2 | ||
| Writer | OST-16 |
And the second in the permissions and objects:
| Role | Permission | Filter | Object |
|---|---|---|---|
| Admin | CRUD | * | tabHome |
| CRUD | * | tabAdmin | |
| Writer | RU | Energy | tabInput |
| R | Energy | tabAdmin | |
| Reader | R | * | tabInput |
| * | tabAdmin |
As can be seen easily the filter has an improvement on the user-role-filter, but does makes the permission objects a mess.
Therefor:
- An extra table has to be created for the filter in the User-Role-Filter.
- The Permissions and objects needs to be made in a specific application-class.
The class example
Create the php classes:
- RBAC_Object
- RBAC_ORP
- RBAC_Operation
|
<syntaxhighlight lang="php" line> /** * Class
class RBAC_ORP { /** @var array The RBAC Objects. */ private $aObjects; /** @var array Multiple Dimension array. */ private $aORP; function init() { $this->aObjects = array(
10 => new RBAC_Object("tabHome" , RBAC_Object::OBJ_PAGE),
20 => new RBAC_Object("tabPrefs" , RBAC_Object::OBJ_PAGE),
21 => new RBAC_Object("tabPrefsGen" , RBAC_Object::OBJ_PAGE),
...
44 => new RBAC_Object("tabHelpAbout" , RBAC_Object::OBJ_PAGE),
/*
90 => new RBAC_Object("tabTest" , RBAC_Object::OBJ_FORM),
*/
);
// Creates the Object-Role-Permission.
$this->aORP = array(
10 => array( 'admin' => RBAC_Operation::OPER_CRUD,
'writer' => RBAC_Operation::OPER_RU,
'reader' => RBAC_Operation::OPER_READ,
'guest' => RBAC_Operation::OPER_READ,
'*' => RBAC_Operation::OPER_READ),
20 => array( 'admin' => RBAC_Operation::OPER_CRUD,
'writer' => RBAC_Operation::OPER_RU,
'reader' => RBAC_Operation::OPER_RU,
'guest' => RBAC_Operation::OPER_READ,
'*' => RBAC_Operation::OPER_NORIGHT),
21 => array( 'admin' => RBAC_Operation::OPER_CRUD,
'writer' => RBAC_Operation::OPER_RU,
'reader' => RBAC_Operation::OPER_RU,
'guest' => RBAC_Operation::OPER_READ,
'*' => RBAC_Operation::OPER_NORIGHT),
...
/*
90 => array( 'admin' => RBAC_Operation::OPER_CRUD),
*/
);
} // init
} </syntaxhighlight> |
<syntaxhighlight lang="php" line> class RBAC_Operation { /** * Operation access parameters. * @type integer/byte */ const OPER_NORIGHT = 0; const OPER_CREATE = 1; const OPER_READ = 2; const OPER_WRITE = 4; const OPER_DELETE = 8; const OPER_LOCKED = 16; const OPER_CRUD = 15; // Create(1) + Read(2) + Write(4) + Delete(8) const OPER_RU = 6; // Read(2) + Write(4) } class RBAC_Object { const OBJ_PAGE = "objectPageTab"; const OBJ_FORM = "objectForm"; /** @var boolean Debug flag. */ protected $debug = false; /** @var string Name of the object/operation. */ private $objectName; /** @var enum type of the object. */ private $objectType; /** @var boolean Locked (not uesed yet). */ public $locked; public function __construct( $name, $type = RBAC_Object::OBJ_PAGE, $debug = false) {
$this->debug = $debug;
$this->objectName = $name;
$this->objectType = $type;
} // __construct
... }
|
See also
- NIST CSC RBAC, National Institute of Standards and Technology (NIST), Computer Security Resource Center (CSRC) Role Base Access Control (RBAC) Presentation.
Reference
- ↑ NIST - CSRC National Institute of Standards and Technology - Computer Security Resource Center - Role Based Access Control.
- ↑ Mind-it, NIST RBAC Data Model