RBAC: Difference between revisions
Jump to navigation
Jump to search
| Line 29: | Line 29: | ||
# Model PHP: https://www.mind-it.info/2009/10/02/a-query-engine-for-php | # Model PHP: https://www.mind-it.info/2009/10/02/a-query-engine-for-php | ||
== | == Examples == | ||
As always an example makes more clear than anything else. | As always an example makes more clear than anything else. | ||
=== Generic example === | |||
Suppose we take a generic app as an example. | Suppose we take a generic app as an example. | ||
The following fictive user and roles are defined: | The following fictive user and roles are defined: | ||
| Line 85: | Line 87: | ||
|} | |} | ||
|} | |} | ||
=== Specific example === | |||
The above generic example has a few disadvantages. | |||
# The application may have different roles for different occurrences in an application. | |||
# The object may have different roles for specific objects inside an application. | |||
In case of the application Energy the user may have different houses and have different roles on those houses. | |||
I call that a filter. | |||
{| class="wikitableharm sortable" width="650px" | |||
! width="200px" | User | |||
! width="200px" | Role | |||
! width="200px" | Filter | |||
|- | |||
| rowspan="3" | Harm | |||
| Admin || NOH-116 | |||
|- | |||
| Admin || AadR-2 | |||
|- | |||
| Admin || OST-16 | |||
|- | |||
| rowspan="3" | Riet | |||
| Writer || NOH-116 | |||
|- | |||
| Reader || AadR-2 | |||
|- | |||
| || OST-16 | |||
|- | |||
| rowspan="3" | Jan | |||
| || NOH-116 | |||
|- | |||
| || AadR-2 | |||
|- | |||
| Writer || OST-16 | |||
|} | |||
And the second in the permissions and objects: | |||
{| class="wikitableharm" width="650px" | |||
! width="200px" | Role | |||
! width="200px" | Permission | |||
! width="200px" | Filter | |||
! width="200px" | Object | |||
|- | |||
| rowspan="2" | Admin | |||
| CRUD || * || tabHome | |||
|- | |||
| CRUD || * || tabAdmin | |||
|- | |||
| rowspan="2" | Writer | |||
| RU || Energy || tabInput | |||
|- | |||
| R || Energy || tabAdmin | |||
|- | |||
| rowspan="2" | Reader | |||
| R || * || tabInput | |||
|- | |||
| || * || tabAdmin | |||
|} | |||
As can be seen easily the filter has an improvement on the user-role-filter, but does makes the permission objects a mess. | |||
<br>Therefor: | |||
# An extra table has to be created for the filter in the User-Role-Filter. | |||
# The Permissions and objects needs to be made in a specific application-class. | |||
== See also == | == See also == | ||
Revision as of 12:05, 7 August 2018
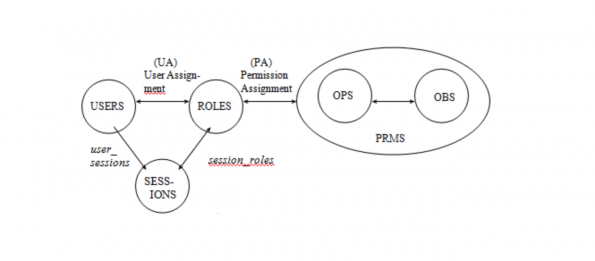
Role Based Access Control (RBAC) is a model for giving a user access to one or more resources.
NIST CSRC RBAC is the de facto implementation [1].
Introduction
RBAC is an access control mechanism which:
- Describes complex access control policies,
- Reduces errors in administration,
- Reduces cost of administration.
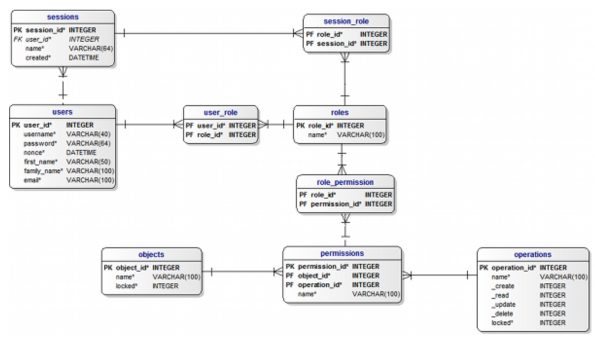
- Model and Entity Relation taken from Mind-it [2].
- Model Database: https://www.mind-it.info/wp-content/uploads/2011/06/mysql_5.txt
- Model PHP: https://www.mind-it.info/2009/10/02/a-query-engine-for-php
Examples
As always an example makes more clear than anything else.
Generic example
Suppose we take a generic app as an example. The following fictive user and roles are defined:
|
|
Specific example
The above generic example has a few disadvantages.
- The application may have different roles for different occurrences in an application.
- The object may have different roles for specific objects inside an application.
In case of the application Energy the user may have different houses and have different roles on those houses. I call that a filter.
| User | Role | Filter |
|---|---|---|
| Harm | Admin | NOH-116 |
| Admin | AadR-2 | |
| Admin | OST-16 | |
| Riet | Writer | NOH-116 |
| Reader | AadR-2 | |
| OST-16 | ||
| Jan | NOH-116 | |
| AadR-2 | ||
| Writer | OST-16 |
And the second in the permissions and objects:
| Role | Permission | Filter | Object |
|---|---|---|---|
| Admin | CRUD | * | tabHome |
| CRUD | * | tabAdmin | |
| Writer | RU | Energy | tabInput |
| R | Energy | tabAdmin | |
| Reader | R | * | tabInput |
| * | tabAdmin |
As can be seen easily the filter has an improvement on the user-role-filter, but does makes the permission objects a mess.
Therefor:
- An extra table has to be created for the filter in the User-Role-Filter.
- The Permissions and objects needs to be made in a specific application-class.
See also
- NIST CSC RBAC, National Institute of Standards and Technology (NIST), Computer Security Resource Center (CSRC) Role Base Access Control (RBAC) Presentation.
Reference
- ↑ NIST - CSRC National Institute of Standards and Technology - Computer Security Resource Center - Role Based Access Control]
- ↑ Mind-it, NIST RBAC Data Model