RBAC: Difference between revisions
Jump to navigation
Jump to search
| Line 28: | Line 28: | ||
# Model Database: https://www.mind-it.info/wp-content/uploads/2011/06/mysql_5.txt | # Model Database: https://www.mind-it.info/wp-content/uploads/2011/06/mysql_5.txt | ||
# Model PHP: https://www.mind-it.info/2009/10/02/a-query-engine-for-php | # Model PHP: https://www.mind-it.info/2009/10/02/a-query-engine-for-php | ||
== Example Energy == | |||
As always an example makes more clear than anything else. | |||
Suppose we take a generic app as an example. | |||
The following fictive user and roles are defined: | |||
{| class="wikitable" width="1100px" | |||
|- style="vertical-align:top;" | |||
| width="33%" | | |||
{| class="wikitableharm" width="450px" | |||
! width="200px" | User | |||
! width="200px" | Role | |||
|- | |||
| Harm || Admin | |||
|- | |||
| Riet || Writer | |||
|- | |||
| Jan || Reader | |||
|- | |||
| Guest || Guest | |||
|} | |||
| width="67%" | | |||
{| class="wikitableharm" width="650px" | |||
! width="200px" | Role | |||
! width="200px" | Permission | |||
! width="200px" | Object | |||
|- | |||
| Admin || CRUD || Energy-tabHome | |||
|- | |||
| Writer || RU || Energy-tabHome | |||
|- | |||
| Reader || R || Energy-tabHome | |||
|- | |||
| Guest || R || Energy-tabHome | |||
|} | |||
|} | |||
== See also == | == See also == | ||
<span class="editsection">[[#content|top]]</span> | <span class="editsection">[[#content|top]]</span> | ||
* [https://csrc.nist.gov/CSRC/media/Presentations/Role-Based-Access-Control-(RBAC)-Presentation/images-media/rbac-slides-doe.pdf NIST CSC RBAC], National Institute of Standards and Technology (NIST), Computer Security Resource Center (CSRC) Role Base Access Control (RBAC) Presentation. | * [https://csrc.nist.gov/CSRC/media/Presentations/Role-Based-Access-Control-(RBAC)-Presentation/images-media/rbac-slides-doe.pdf NIST CSC RBAC], National Institute of Standards and Technology (NIST), Computer Security Resource Center (CSRC) Role Base Access Control (RBAC) Presentation. | ||
== Reference == | == Reference == | ||
Revision as of 10:55, 7 August 2018
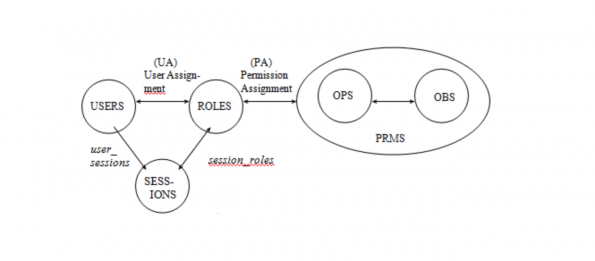
Role Based Access Control (RBAC) is a model for giving a user access to one or more resources.
NIST CSRC RBAC is the de facto implementation [1].
Introduction
RBAC is an access control mechanism which:
- Describes complex access control policies,
- Reduces errors in administration,
- Reduces cost of administration.
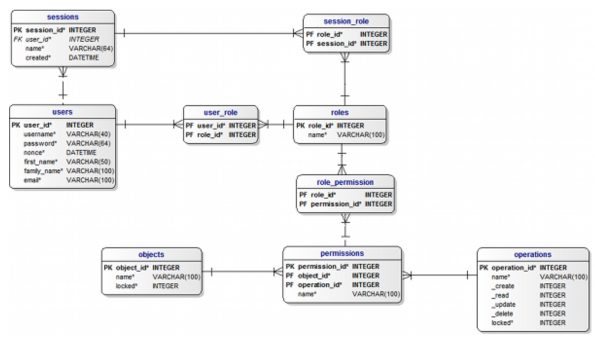
- Model and Entity Relation taken from Mind-it [2].
- Model Database: https://www.mind-it.info/wp-content/uploads/2011/06/mysql_5.txt
- Model PHP: https://www.mind-it.info/2009/10/02/a-query-engine-for-php
Example Energy
As always an example makes more clear than anything else. Suppose we take a generic app as an example. The following fictive user and roles are defined:
|
|
See also
- NIST CSC RBAC, National Institute of Standards and Technology (NIST), Computer Security Resource Center (CSRC) Role Base Access Control (RBAC) Presentation.
Reference
- ↑ NIST - CSRC National Institute of Standards and Technology - Computer Security Resource Center - Role Based Access Control]
- ↑ Mind-it, NIST RBAC Data Model