RBAC: Difference between revisions
Jump to navigation
Jump to search
mNo edit summary |
|||
| Line 25: | Line 25: | ||
# operation: operations are the actions that are performed on the objects | # operation: operations are the actions that are performed on the objects | ||
|} | |} | ||
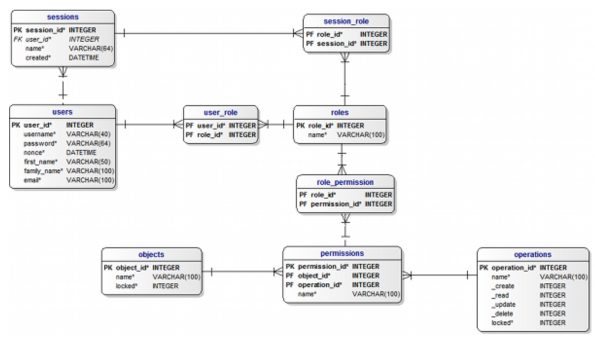
# Model and Entity Relation taken from Mind-it <ref>[https://www.mind-it.info/2010/01/09/nist-rbac-data-model Mind-it], NIST RBAC Data Model</ref>. | |||
# Model Database: https://www.mind-it.info/wp-content/uploads/2011/06/mysql_5.txt | |||
# Model PHP: https://www.mind-it.info/2009/10/02/a-query-engine-for-php | |||
== See also == | == See also == | ||
Revision as of 17:43, 6 August 2018
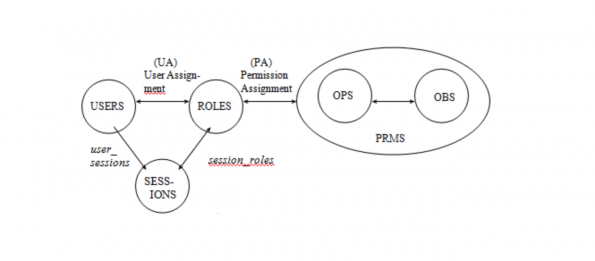
Role Based Access Control (RBAC) is a model for giving a user access to one or more resources.
NIST CSRC RBAC is the de facto implementation [1].
Introduction
RBAC is an access control mechanism which:
- Describes complex access control policies,
- Reduces errors in administration,
- Reduces cost of administration.
- Model and Entity Relation taken from Mind-it [2].
- Model Database: https://www.mind-it.info/wp-content/uploads/2011/06/mysql_5.txt
- Model PHP: https://www.mind-it.info/2009/10/02/a-query-engine-for-php
See also
- NIST CSC RBAC, National Institute of Standards and Technology (NIST), Computer Security Resource Center (CSRC) Role Base Access Control (RBAC) Presentation.
Reference
- ↑ NIST - CSRC National Institute of Standards and Technology - Computer Security Resource Center - Role Based Access Control]
- ↑ Mind-it, NIST RBAC Data Model